Application Security
Secure Your Applications From The Ground Up With Powerful App Security Service.
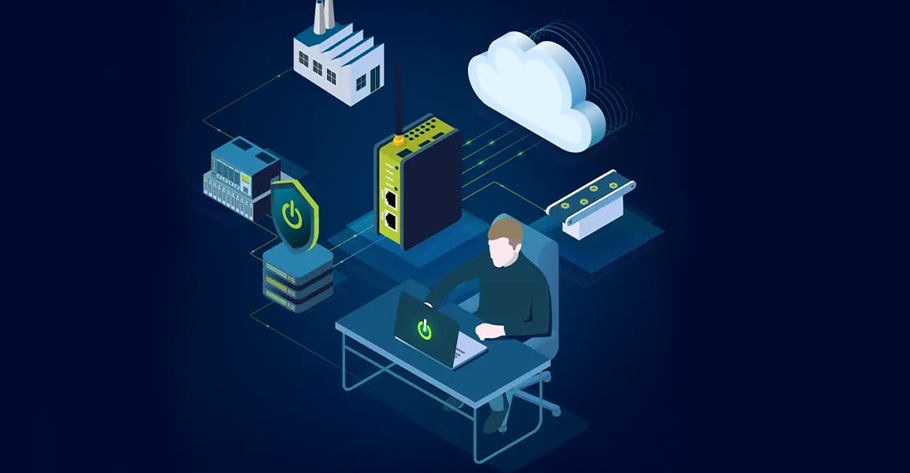
With TSCTI’s Application Security Service, you get robust security solutions for your applications running in the cloud. We offer 24*7 protection for your applications from cyber threats such as hacking, data breaches, and other malicious attacks. Our service provides your organization with a more cost-effective and efficient way to secure your applications in the cloud, allowing you to focus on your core business operations.
Secure Your Applications in the Cloud with TSCTI’s Scalable, Cloud-Based Application Security
Don't leave your applications vulnerable, choose TSCTI’s trusted Application Security.
Compliance
TSCTI ensures that your application meets industry-specific compliance and regulatory requirements, such as HIPAA, PCI-DSS, and GDPR.
View Case Studie DetailsFaster Deployment
TSCTI’s application security is designed to be very fast and easy to deploy, with a short deployment time, offers immediate value to its users, and doesn’t disrupt their workflows or cause any issues for them.
View Case Studie DetailsCost-Effective
By using our application security service, you can benefit from increased application security without having to invest in expensive solutions or hire dedicated security personnel, resulting in significant cost savings.
View Case Studie DetailsExpert Security team
TSCTI’s security experts have years of experience in the field of application security and are always up-to-date on the latest security trends and threats, ensuring that your applications are always protected against the latest security risks.
View Case Studie DetailsWhy should you choose TSCTI’s Application Security?
Our application security offerings are custom-tailored to meet each of our client’s unique set of security challenges and requirements.
- Hassle-Free Security Management
- Wide Range of Security Features
- Cloud-Based Architecture
- Customizable Policies
- Centralized Network Visibility
Hassle-Free Security Management
TSCTI takes care of all aspects of application security management, including 24*7 monitoring and managing the security of your applications, freeing up your team to focus on core business operations.

Wide Range of Security Features
We offer a wide range of security features, including vulnerability assessments, real-time threat detection, 24*7 active remediation, web application firewalls, and access controls, ensuring comprehensive coverage for your applications.

Cloud-Based Architecture
Our security solutions are typically hosted in the cloud, offering several technical benefits such as scalability, resilience, and easy access to data.
Customizable Policies
TSCTI has flexible app security solutions that can be customized to meet specific security policies and requirements, enabling organizations to tailor their security solutions to fit their unique needs and preferences.

Centralized Network Visibility
Our team provides 24*7 monitoring and management of all the network traffic for organizations with complex network infrastructure and various endpoints.

Advanced Security Services To Protect Your Application Against Various Cyber Threats.

Attack Simulation
TSCTI can integrate its application security with development tools like continuous integration and deployment (CI/CD) pipelines to facilitate automated security testing. We help businesses identify and address security issues before they can be exploited by attackers.

Automated vulnerability scanning
TSCTI’s application security solution scans your application for known vulnerabilities using automated tools, which helps to identify and prioritize potential security issues.

Manual Penetration Testing
By simulating attacks on the application, we help identify and exploit vulnerabilities that may have been missed by automated scanning tools.

Malware Detection & Removal
With our penetration testing service, we help businesses identify potential vulnerabilities in the network and assess the effectiveness of network security controls.

Reporting & Analytics
Get regular reports and analytics on the security posture of the web application, such as vulnerability scan results, penetration test findings, and WAF logs.
Secure Your Apps with Ease by Choosing TSCTI’s Application Security Service
Get your applications secured without any hassle and keep your data safe with TSCTI’s Application Security Service. Get the peace of mind you need, knowing that your apps are protected with the highest level of security.